Container and Kubernetes Security
Container & Kubernetes Security
Reduce risk in containerized applications across the development lifecycle. Leverage Wiz container, Kubernetes and cloud risk engines to identify the most critical risks affecting your containers and prioritize remediation.
Cross-Cloud Contextualized Container & Kubernetes Security
Complete agentless visibility to your containers and Kubernetes clusters across clouds and architectures. Graph-based container & Kubernetes security that spans the full risk landscape of your environments across containers, Kubernetes and cloud risks.
Complete Agentless Visibility
Discover and scan your containers, hosts, and clusters across cloud-managed and self-managed Kubernetes, serverless containers, and standalone containers running on virtual machines.
Kubernetes & Cloud Deep Risk Assessment
Assess container risks in runtime by combining data from containers, hosts, cloud providers and Kubernetes APIs to identify container and host vulnerabilities and misconfigurations, internet-facing containers, excessive permissions, and exposed secrets.
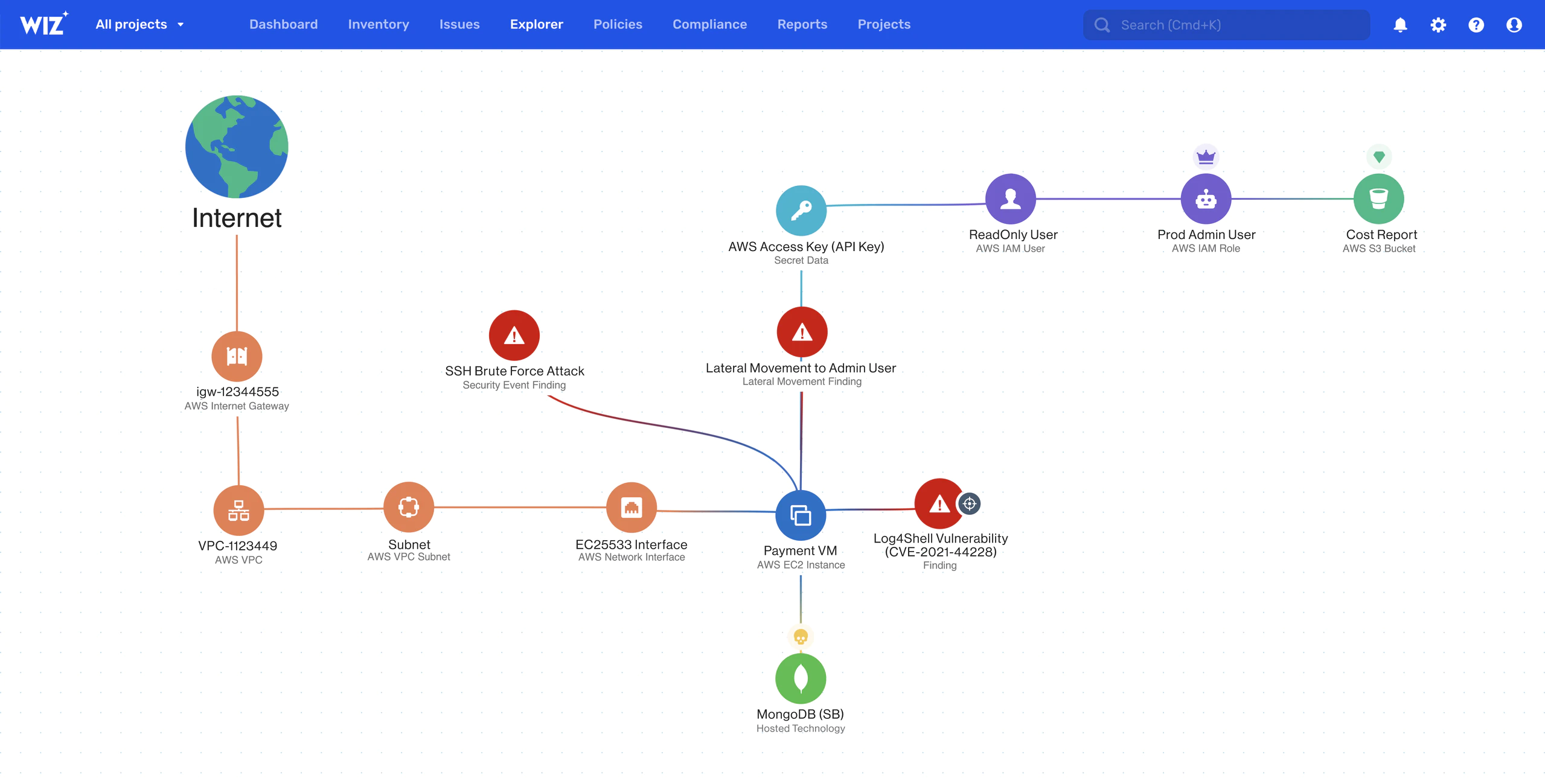
Graph-Based Prioritization
Correlate multiple risk factors across containers, hosts, Kubernetes clusters, and the cloud environment to identify the most critical risks and prioritize remediation.
Secure Container Images Across the Lifecycle
Build: Scan container images in the CI/CD pipeline to detect vulnerabilities and exposed secrets before pushing images to the registry. Registry: Regularly scan images in container registries to detect vulnerabilities and security risks before deployment to the runtime environment. Run: Scan images of running containers for vulnerabilities, malware, exposed secrets, and misconfigurations using agentless scanning.
Graph-Based Risk Correlation and Prioritization
Correlate multiple risk factors across containers, hosts, Kubernetes clusters and the cloud environment to identify the most critical risks and prioritize remediation.
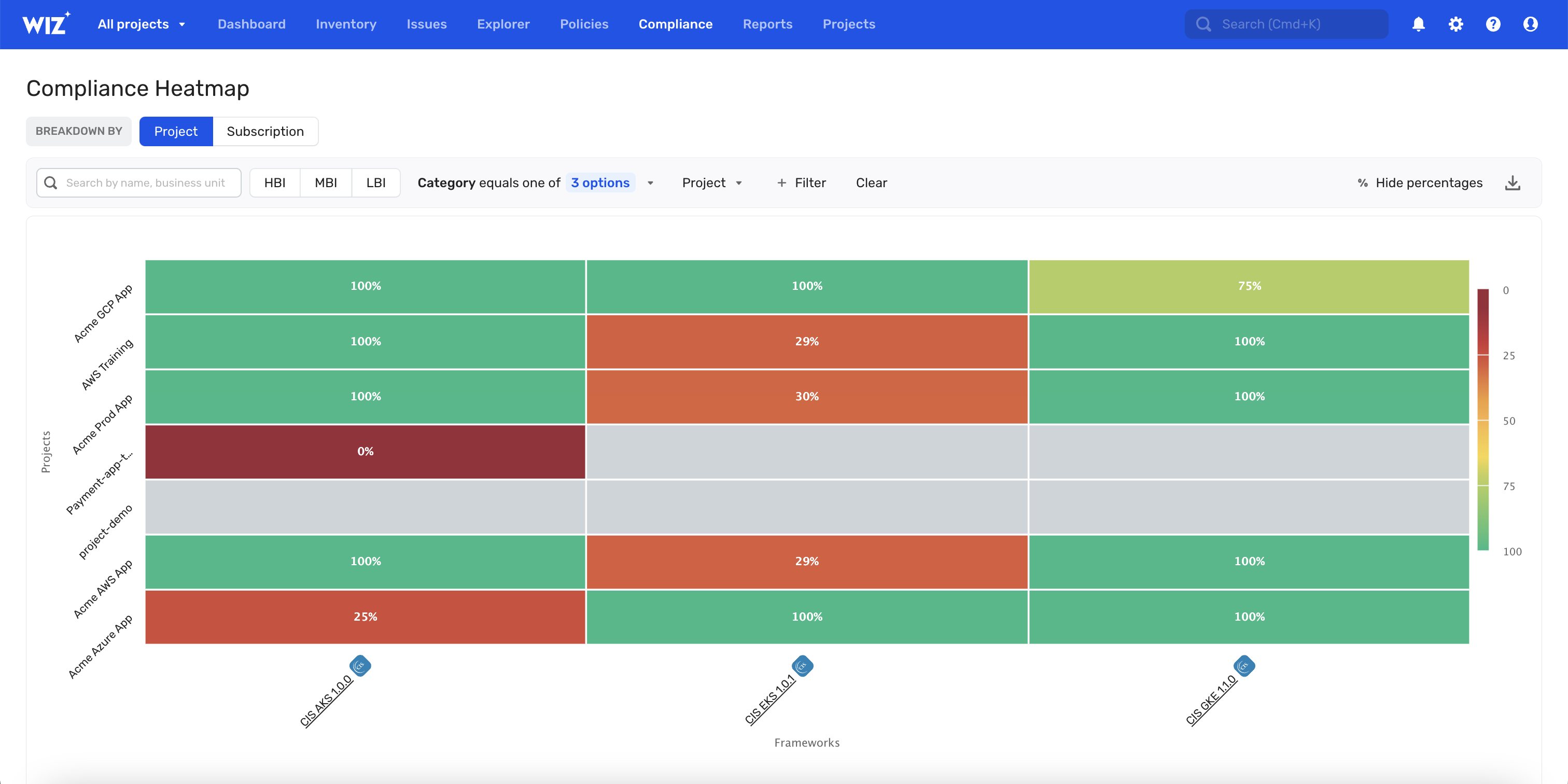
Automatic Kubernetes Security Posture Management (KSPM)
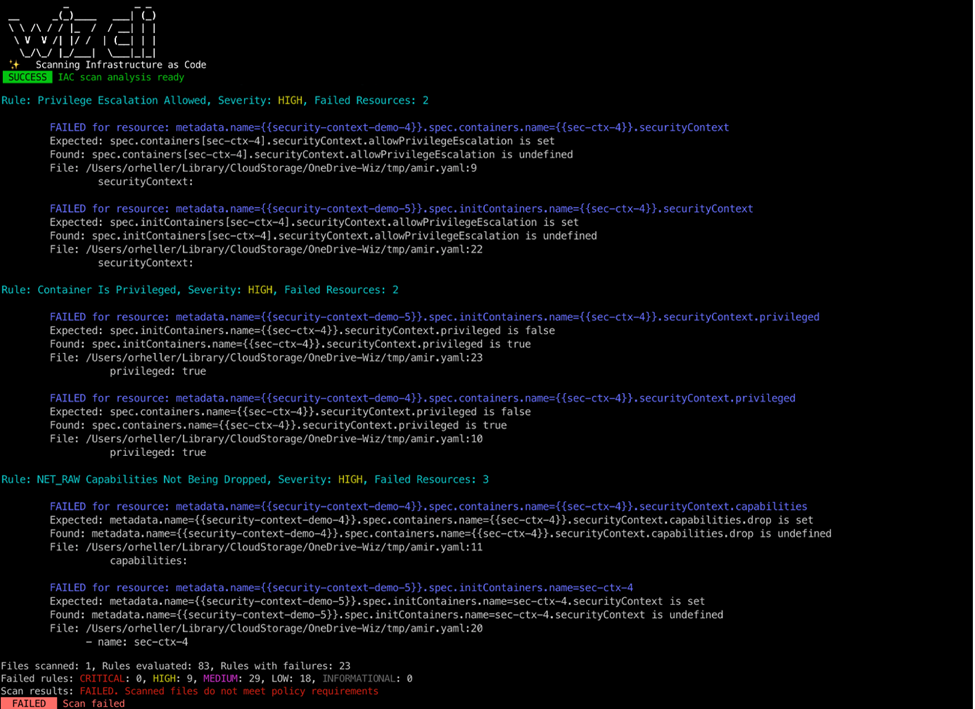
IaC Security in the CI/CD Pipeline
Scan Infrastructure-as-code (IaC) files across Dockerfiles, Kubernetes YAML manifests, and Helm charts for misconfigurations and security risks. Automatically assess one security policy across your cloud and Kubernetes development lifecycle and decide whether to block builds that violate it.
Getting started is easy
Complete security for AWS, Azure, GCP, OCI, Alibaba Cloud, Kubernetes, and Openshift. Start securing your cloud with a 5 minute agentless install. Meet your new partner in cloud security.