Cloud Infrastructure Entitlement Management
Cloud Infrastructure Entitlement Management
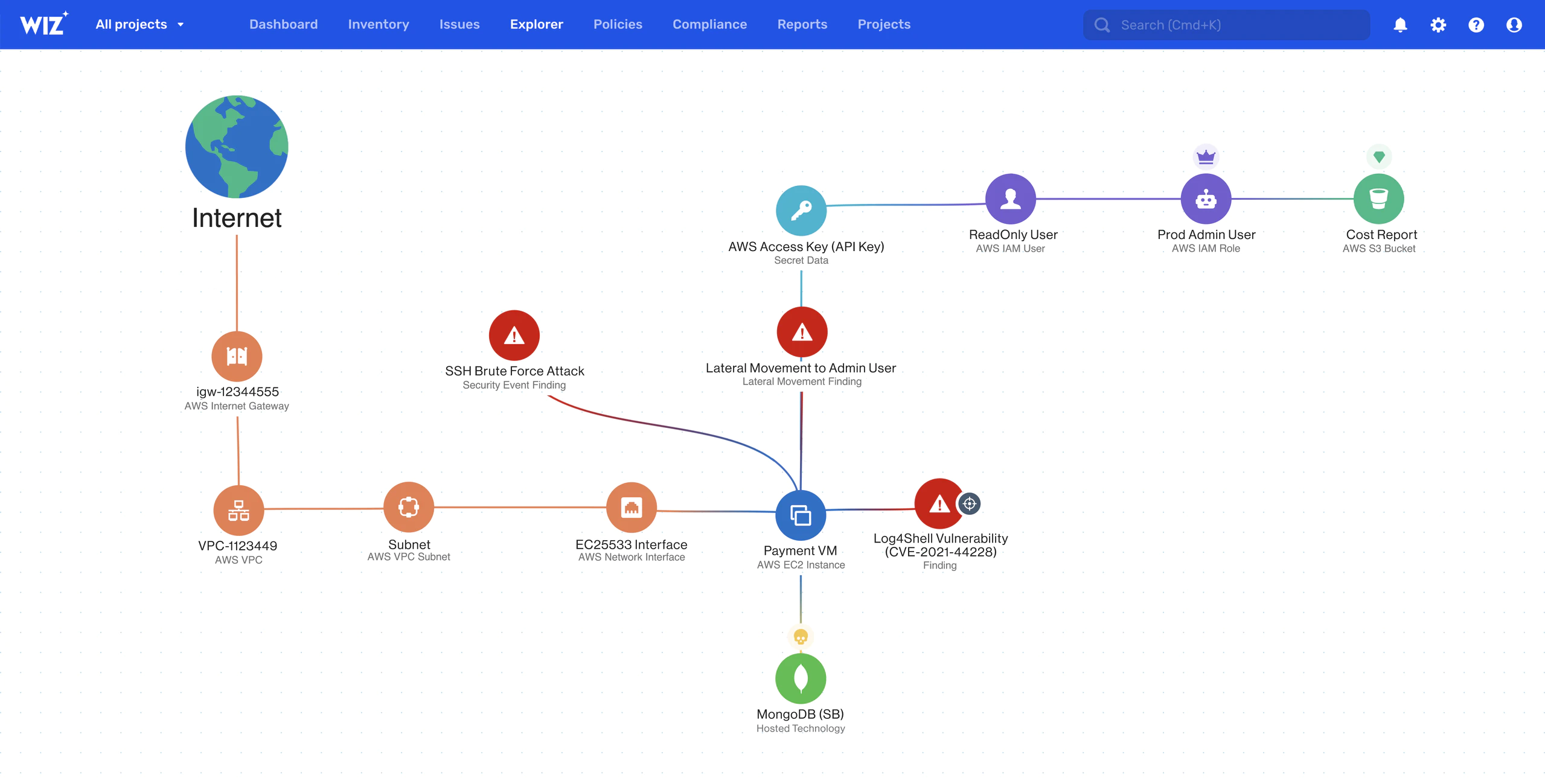
Wiz analyzes cloud entitlements and auto-generates least privilege policies across your cloud, to help teams visualize, detect, prioritize, and remediate identity (IAM) risks.
Take Control of Your Cloud Entitlements
Wiz analyzes cloud entitlements and effective permissions to help teams understand their identity-related risk and exposure. Wiz scans and detects exposed secrets and lateral movement paths that might compromise sensitive assets and auto-generates remediation suggestions and least privilege policies.
Right-Size Permissions
Monitor human and service identities and utilize the auto-generated guided least privilege suggestions to right-size the access and entitlements in your environment.
Analyze Effective Permissions
Wiz builds a map of effective access between all principals and all resources, taking into account advanced cloud-native mitigating controls including boundaries, ACLs and SCPs.
Exposed Secrets and Lateral Movement
Agentless and frictionless detection of leaked secrets or credentials that attackers might use in attempts to access sensitive assets or take over accounts.
Enforce Least Privilege Across Your Clouds
Understand effective permissions: Wiz analyzes effective permissions to help teams understand the bottom line of “who has access to what.” Auto-generated recommendations: Based on usage, Wiz automatically generates granular recommendations that allow teams to follow guided remediation steps to reduce access and revoke unused permissions. Reduce IAM exposure: Wiz provides explicit granular recommendations on how to close and remediate any public exposure via IAM.
Wiz detects accidental exposure of sensitive resources via identity misconfigurations, and enables teams to quickly act and remediate.
Go Beyond CIEM
Getting started is easy
Complete security for AWS, Azure, GCP, OCI, Alibaba Cloud, Kubernetes, and Openshift. Start securing your cloud with a 5 minute agentless install. Meet your new partner in cloud security.